OUR TECHNOLOGY
Technology That Adapts to You
Technology should be a solution, not a challenge. We deliver systems that are easy to integrate, scalable, and built on industry standards to keep your business competitive in the digital era.
Operating System & Database Independent
Our application is designed to be platform-independent, giving you the flexibility to run it on your preferred operating system, whether it’s Microsoft Windows or Linux. Additionally, it supports a wide range of database systems, including MS SQL Server, Oracle, and MySQL, allowing seamless integration with your existing infrastructure.


Operating System & Database Independent
Our application is designed to be platform-independent, giving you the flexibility to run it on your preferred operating system, whether it’s Microsoft Windows or Linux. Additionally, it supports a wide range of database systems, including MS SQL Server, Oracle, and MySQL, allowing seamless integration with your existing infrastructure.
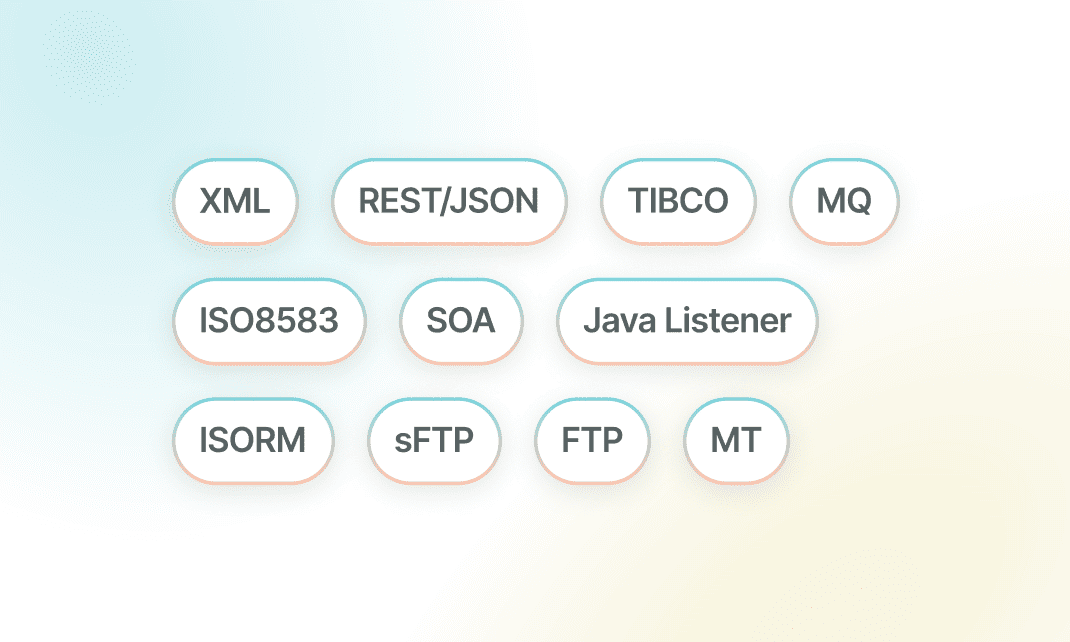
Interface
Our application is designed to be platform-independent, giving you the flexibility to run it on your preferred operating system, whether it’s Microsoft Windows or Linux. Additionally, it supports a wide range of database systems, including MS SQL Server, Oracle, and MySQL, allowing seamless integration with your existing infrastructure.
Open API
Integrating processes from other systems, that your customer owns, such as Enterprise Resource Planning (ERP) system, other Hosts, CRM, Point of Sales, Accounting System, etc will allow a better management experience. Open API management technology makes the integration possible with secure and fast message signing, end-to-end encryption and signature validity to ensure all messages are authenticated.
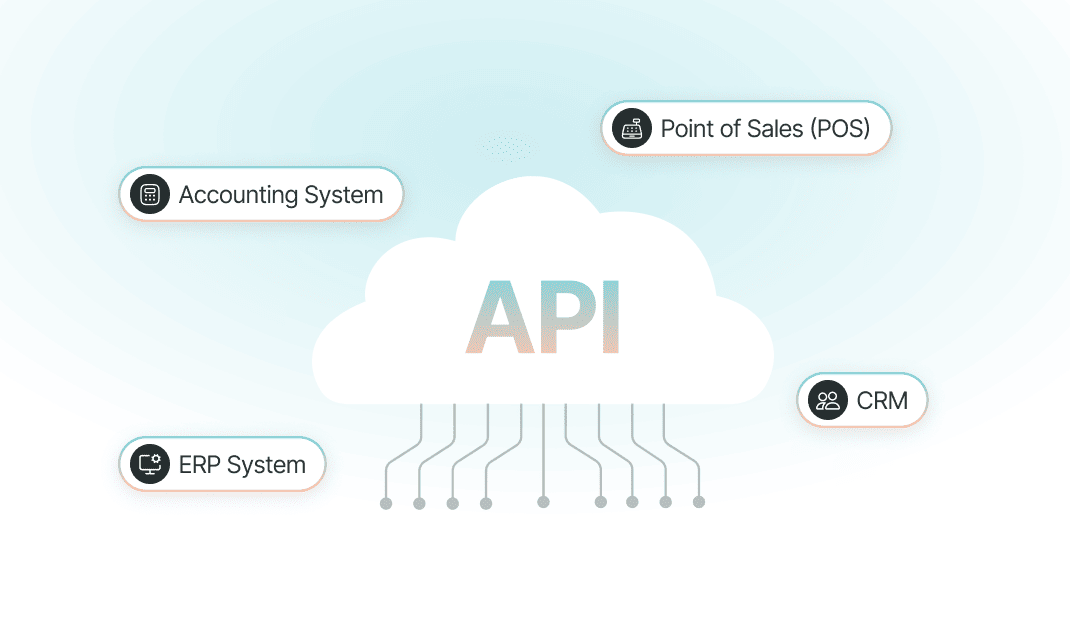

Open API
Integrating processes from other systems, that your customer owns, such as Enterprise Resource Planning (ERP) system, other Hosts, CRM, Point of Sales, Accounting System, etc will allow a better management experience. Open API management technology makes the integration possible with secure and fast message signing, end-to-end encryption and signature validity to ensure all messages are authenticated.
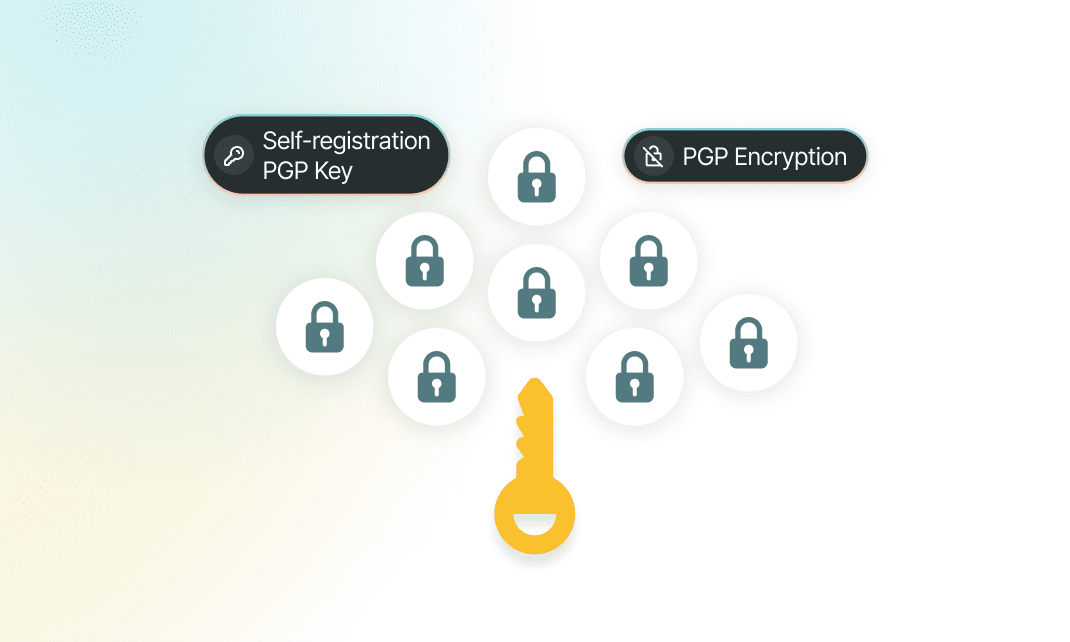
File Interchange
Sometimes systems need to be isolated and cannot directly be connected to the external host, thus a file interchange solution will solve the problem. With self-registration PGP key, and PGP encryption, our system can interchange (send – receive) files to an sFTP server. This method requires minimum modification to the customer’s system.
Multiple Deployment Support
Our platform is designed to support container-based deployments, enabling efficient scalability, rapid deployment, and seamless integration across diverse IT environments — including traditional (bare metal), virtualized, and containerized systems, whether on-premise or in the cloud.
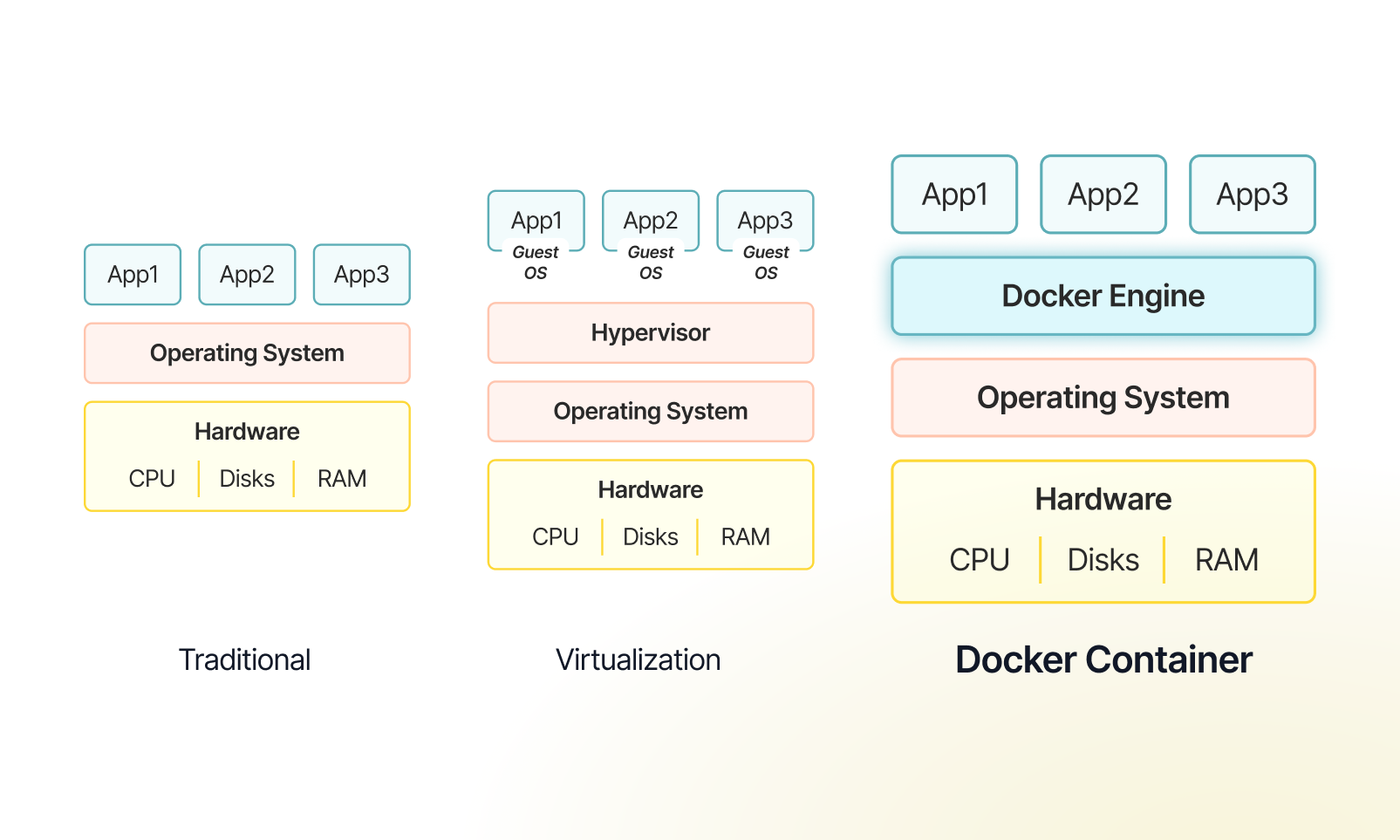

Multiple Deployment Support
Our platform is designed to support container-based deployments, enabling efficient scalability, rapid deployment, and seamless integration across diverse IT environments — including traditional (bare metal), virtualized, and containerized systems, whether on-premise or in the cloud.
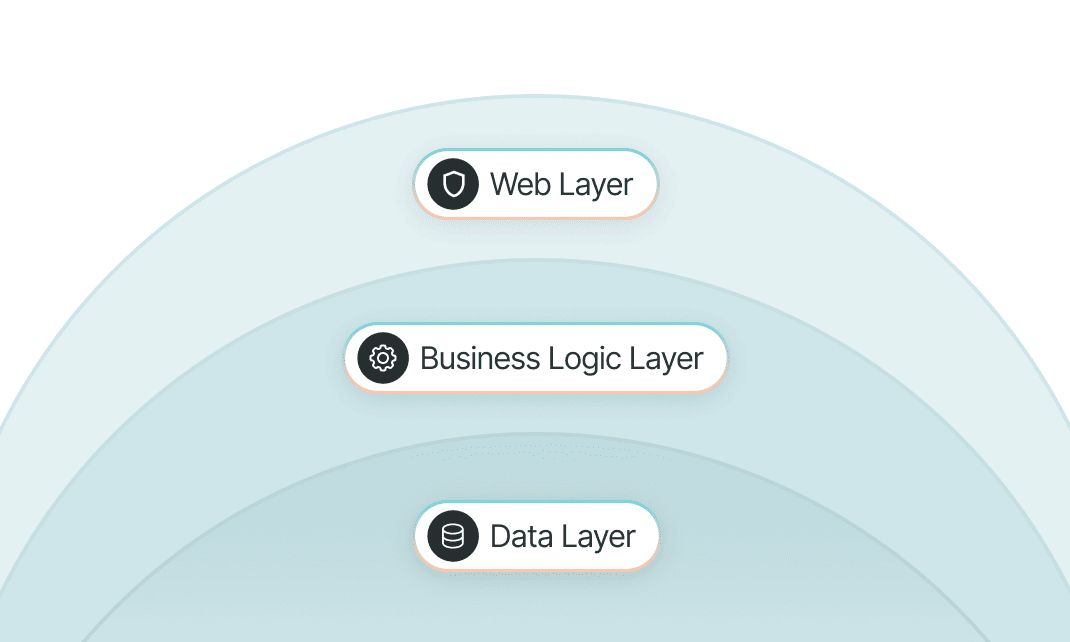
3 Tier
3 layers application architecture provides an extra secure application platform. The first layer will handle web-requests and sessions, meaning any attempt of attack such as DDoS, injection, etc will be contained within this layer. The second layer will handle business processes and lastly, the third layer will be on data-store.
OWASP Standard
SGO systems are developed to meet the OWASP Standard to secure web applications. We apply OWASP Top Ten as best practice.
- A1: Injection
- A2: Broken authentication
- A3: Sensitive data exposure
- A4: XML external entities (XXE)
- A5: Broken access control
- A6: Security misconfiguration
- A7: Cross-site scripting (XSS)
- A8: Insecure deserialization
- A9: Using components with known vulnerabilities
- A10: Insufficient logging and monitoring
owasp.org
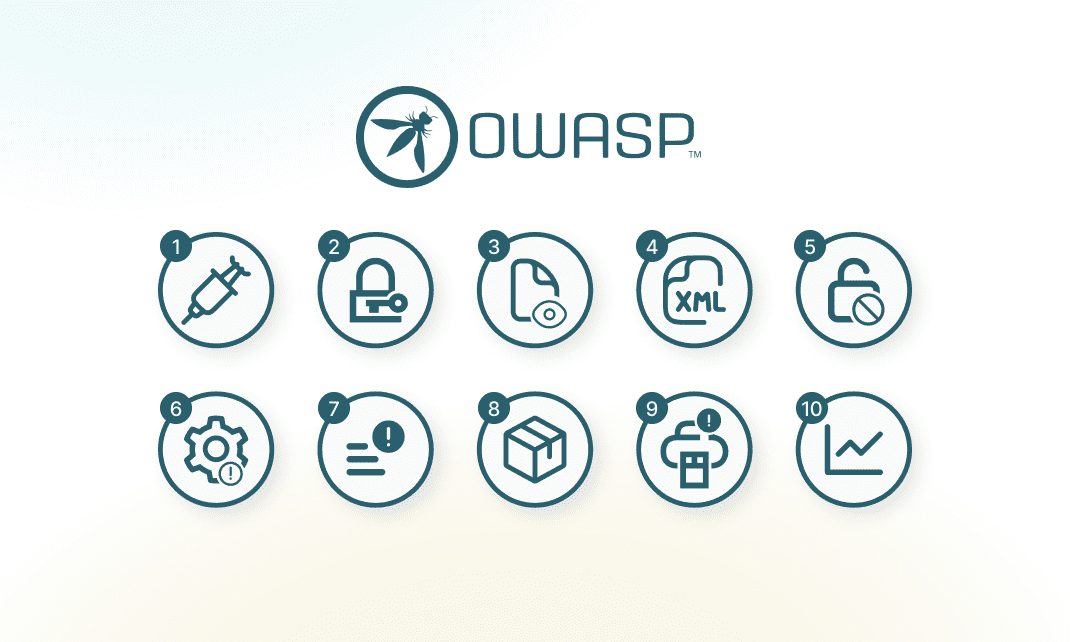

OWASP Standard
SGO systems are developed to meet the OWASP Standard to secure web applications. We apply OWASP Top Ten as best practice.
- A1: Injection
- A2: Broken authentication
- A3: Sensitive data exposure
- A4: XML external entities (XXE)
- A5: Broken access control
- A6: Security misconfiguration
- A7: Cross-site scripting (XSS)
- A8: Insecure deserialization
- A9: Using components with known vulnerabilities
- A10: Insufficient logging and monitoring
owasp.org